How much do you love online content? So much you pay for everything you can? Or do you, like the overwhelming majority of internet users, accept advertising and tracking as a way of life?
1. Panopticlick
Panopticlick is one of the first sites to check out. Panopticlick analyzes your current browser setup, including add-ons and extensions, to measure just how many trackers are tracing your browser session.
This Electronic Frontier Foundation (EFF) research project takes it one step further by detailing unique configuration features that make your browser more noticeable amongst tracking data.
How to Use Panopticlick
Head to the Panopticlick site and hit the giant orange “Test Me” button. Wait for the analysis to complete. Remember, you will experience different levels of tracking, depending on your list of add-ons and extensions.
Note that your browser may refresh several times while this test is running. Don’t panic—just wait for it to complete.
2. Am I Unique?
Am I Unique? is a tracker analyzer with a focus on the unique fingerprint your browser broadcasts. Browsers are relatively unique and are frequently used to identify you online.
Am I Unique takes a fingerprint of your system and adds it to its own database, adding a four-month cookie to your system in the process. You can then head back to the site in a few weeks and examine the changes to your browser fingerprint and if you have become more or less unique.
How to Use Am I Unique?
Head to the Am I Unique site and hit the View My Browser Fingerprint button. Wait for the analysis to complete, then check your results.
If you want to periodically analyze your fingerprint evolution, head to the “My timeline” tab in the left-hand menu column. Download the add-on for your browser (there is support for Chrome and Firefox) and check it periodically for changes.
3. Disconnect
Disconnect features in many tracker-blocking lists and for a good reason. The browser extension blocks over 2,000 individual trackers from following you around the internet. Not only that, but by blocking such a vast amount of trackers, websites actually load faster—up 27 percent faster, according to Disconnect.
The best Disconnect feature, however, is the option to allow some trackers and not others. If you’re a discerning internet user, you whitelist the sites that give you great content for free. MakeUseOf, for instance.
How to Use Disconnect
Using Disconnect is extremely easy. First, head to the Disconnect site and hit the “Get Disconnect” button. Disconnect is currently available for Chrome, Firefox, Safari, and Opera (download links below). Once you install Disconnect, head to a website, and open the extension. The drop-down panel shows you the entire range of trackers currently jotting down your browser session.
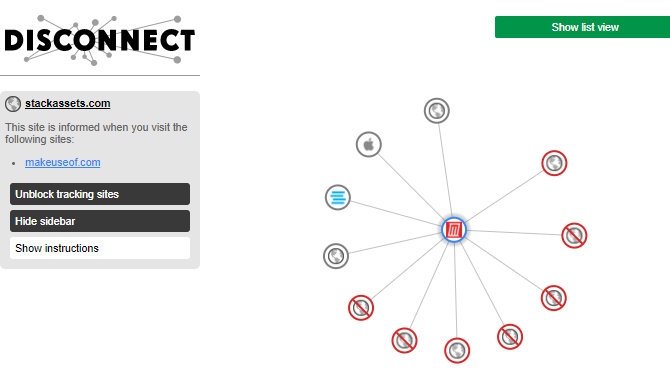
Unlike Panopticlick and Am I Unique, Disconnect lets you visualize the trackers, too. Again, this depends on your other browser settings, but you should see some trackers directly connecting to the site. Some might be harmless or relate to your work or business, so be mindful of precisely what you’re turning off. Disconnect is just one of the many privacy and tracking tools available for Google Chrome.
4. Thunderbeam—Lightbeam for Chrome
Lightbeam is a visual aid to online trackers, displaying the extremely tangled web of trackers between individual sites you visit. Lightbeam was previously a Firefox-only privacy tool. Unfortunately, the Firefox version is no longer available, but there is now an open-source version available for Chrome.
How to Use Lightbeam
Head to the Lightbeam extension page and add it to your browser. Open the extension by clicking the Lightbeam icon in the top-right corner of the browser.
![]()
You arrive at an empty graph. You can quickly populate the graph by heading to some of your favorite sites. Each site will populate the graph with its associated trackers. As you visit more sites, the links between them grow, quickly creating a spaghetti monster of tangled lines. It perfectly illustrates which trackers are following you.
The only downside is that the new version is lacking the website logos from the old version. You can hover over each circle to reveal the site, but the website favicons made it simple to see which sites are tracking you.
5. Trackography
Trackography is your third visual tracker-guide, this time with a more interactive take. Trackography, developed by the Tactical Technology Collective, is an open-source project aiming to “lift the veil on the global tracking industry” by visualizing the vast array of trackers following you around the internet.
You can use Trackography to check:
- Which companies are tracking you.
- The countries hosting the servers of those tracking companies.
- Countries hosting the servers of the website you’re viewing.
- The countries hosting the network infrastructure required to access those media servers and tracking companies.
- Further information on how tracking companies handle your data with regards to their privacy policies.
Overall, Trackography is a great visual resource if you want to understand more about the flow of data tracking around the globe, and where you fit into it.
How to Use Trackography
Head to the Trackography site. Select your host nation. Next, select a media website you want to connect to. Connection lines will immediately spread from your host nation, illustrating the path your data takes, as well as the multiple locations you had no idea your data was traveling through.
Blocking the Trackers
Several exceptional tools stop trackers following you around the internet (as well as cleaning up your online presence):
- uBlock Origin: Block trackers, malicious advertising servers, malware, and more.
- HTTPS Everywhere: Enable HTTPS to protect your data in transit.
- NoScript: Block background scripts.
- Privacy Badger: Block trackers and unwanted cookies.
- PixelBlock: Block tracking pixels in Gmail.
- Google Activity Controls: control what Google remembers about your searches.
- deseat.me: Delete your old online accounts in a single click.
- Tor Browser: Uses built-in script blocking and onion routing protocol to protect your privacy.
- DuckDuckGo: Search the internet without trackers taking note.
This list isn’t exhaustive, but it will set you on the right path to avoiding trackers where possible.
Online Tracking Is Endless
The 2018 Facebook revelations pushed online tracking and data collection further into the public eye than before. For many, it was the first realization that everything they do, say, watch, and read online is likely recorded—and out of their control.















/cdn.vox-cdn.com/uploads/chorus_image/image/67085699/DSCF7265.0.jpg)
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/20103528/DSCF7267.jpg)
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/20103529/DSCF7266.jpg)

